 https://www.synyo.com/wp-content/uploads/SYNYO-NEWS-featured-image-NEW01007705EN.png
400
459
leo
https://www.synyo.com/wp-content/uploads/2017/09/synyo-logo.png
leo2025-01-01 10:47:112025-02-10 10:48:51BOND: Outcomes in Advancing Education, Tolerance and Heritage Preservation to combat Antisemitism
https://www.synyo.com/wp-content/uploads/SYNYO-NEWS-featured-image-NEW01007705EN.png
400
459
leo
https://www.synyo.com/wp-content/uploads/2017/09/synyo-logo.png
leo2025-01-01 10:47:112025-02-10 10:48:51BOND: Outcomes in Advancing Education, Tolerance and Heritage Preservation to combat AntisemitismNOTIONES

NOTIONES: Emerging technologies in the fields of security and intelligence
To map emerging technologies, which are most promising in the fields of intelligence and security, NOTIONES exploited open databanks of publications and patents. The information was gathered via targeted search based on keywords and by the means of technology horizon scanning and exploration of the CORDIS projects database.
Horizon Scanning
Horizon scanning” was intended as a systematic research of relevant technological developments with the purpose of highlighting opportunity and threats that may influence the capability of organizations and bodies providing intelligence and security services to achieve their objectives ad goals.
Focus areas
The focus areas tackled during the horizon scanning task were namely:
- Technological Solutions to Secure Data Sharing and Dissemination (internally and externally);
- Improvements and Innovations to Various Intelligence Related Training.
The Figure 1 illustrates the approach, which was applied by the project to conduct the intended “Horizon scanning”, and thus identify potential capability gaps and innovation needs. At the time of the conduction of the scanning, the diagram appeared jangly due to its exploratory nature.
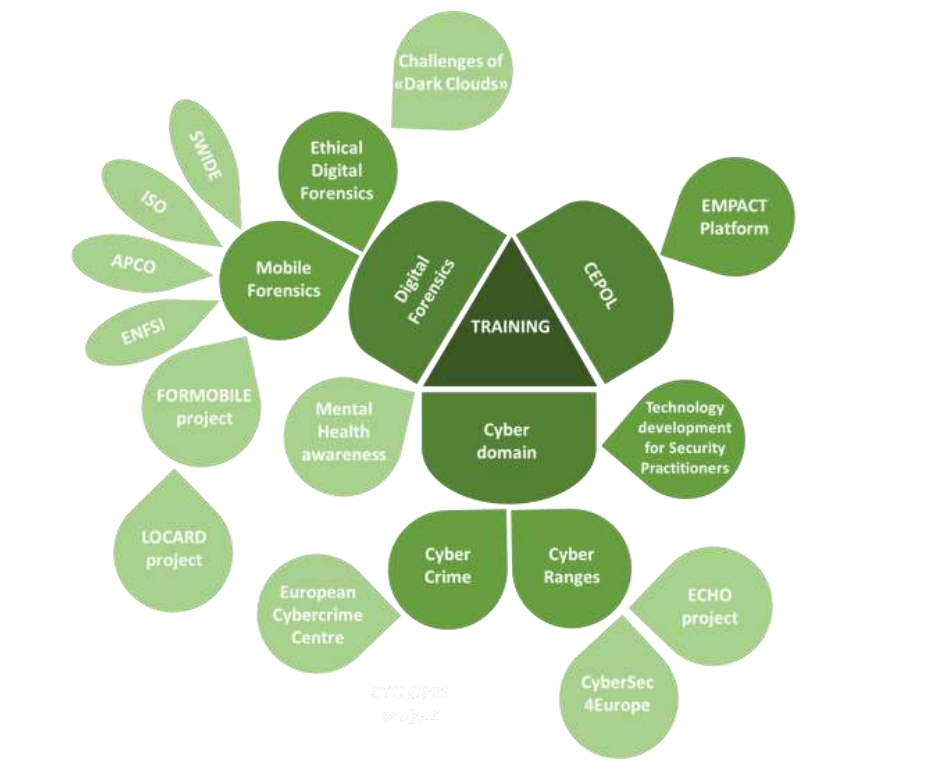
Figure 1: Diagram of the horizon scanning research
The “Horizon Scanning” search led to 59 results as briefly outlined below.
Mental Health
A relevant number of the results referred to training guidelines for Law Enforcement addressing mental health issues, such as publications about the enhancement of intellectual disability awareness amongst law enforcement officers [1] [2] or about the need to increase mental health literacy in law enforcement [3] [4], or about the need to facilitate the referral of persons with suspected mental illnesses to mental health services by law enforcement officers [5].
Another publication reported a framework for ethical digital forensics investigations called PRECEPT (Privacy-Respecting Ethical framework) [6]. The paper “argues the need for a practical, ethically grounded approach to digital forensic investigations, one that acknowledges and respects the privacy rights of individuals and the intellectual capital disclosure rights of organizations, as well as acknowledging the needs of law enforcement”, deriving a set of ethical guidelines, and then mapping these onto a forensics investigation framework.
Mobile Forensics
A very interesting work was retrieved, on Law enforcement educational challenges for mobile forensics [7] by Humphries et al. The paper reports on the debate surrounding standardisation and certification within digital forensics. Several accreditation programs, processes, standards, and best practices were presented in the past, and best practices have been identified: these include, for example, the Good Practice Guideline by the Association of Chief Police Officers of England, Wales and Northern Ireland (APCO) [8], the ISO/IEC 17025 Forensic Lab Accreditation Process [9], and Best practice manual for the forensic examination of digital technology by the European Network for Forensic Science Institutes (ENFSI) [10].
Cybercrime
The search for training also led to results related to cybercrime awareness for law enforcement officers. One of the papers reviewed in-depth, common, cybersecurity countermeasures including legislation, law enforcement, hands-on training, and education among others, with a focus on phishing attacks [11]. The authors stated that many other countries have enacted similar laws for combatting phishing and other cybercrimes. According to the references sources, legislation should be designed to provide large-scale damage against individual phishers or secondary liability against Internet Service Providers (ISPs) in hopes that ISPs will be motivated to play their role in fighting phishing under the auspices of intellectual property or unfair competition laws.
Cybersecurity
Another result of the search referred to Cybersecurity and related training, in particular the emerging relevance of Cyber Ranges [12]. According to the European CyberSecurity Organization (ECSO), “a cyber range is a platform for the development, delivery and use of interactive simulation environments. A simulation environment is a representation of an organisation’s ICT, OT, mobile and physical systems, applications and infrastructures, including the simulation of attacks, users and their activities and any other Internet, public or third-party services which the simulated environment may depend upon”. [13]
Research monitoring on EU projects
A search on the European Community CORDIS (Community Research and Development Information Service) Platform was performed, about the most promising research projects in the field of intelligence and security.
For this analysis, the spotlight was set on projects starting in 2018, highlighting newly financed projects. Such a search resulted in a list of 75 interesting projects, which were investigated one by one to evaluate them on the basis of alignment and interest of their objective and results concerning the NOTIONES aims. After the evaluation, 60 projects were selected out of the initial 75. These were further investigated by examining in deep of the projects’ objectives and results. 41 of these projects were found to have interesting results in terms of available software or modelling, or terms of relevance for the identified focus areas, and were further investigated. The collected projects covered the following research topics/technological areas:
- Various challenges in monitoring and collecting data from the dark web
- Technological needs, solutions, and improvements to the intelligence analysis phase of the Intelligence cycle
- Technological Solutions to Secure Data Sharing and Dissemination (internally and externally)
- Cybersecurity and cybercrime
- Artificial Intelligence and
- Other technological innovation areas – including platforms, CBRNE tools, training for LEAs etc.
Results
The results of the conducted research highlighted technologies and EU projects that are most promising for the purposes of NOTIONES:
- INSPECTr project;
- I-LEAD project;
- LAW-GAME project;
- Cyber ranges;
- P300 technology.
The main findings were also added in the NOTIONES CTI Catalogue and the information was also forwarded for further elaboration to the next tasks in project implementation
Links
https://cordis.europa.eu/
Resources
[1] F. LA, «Method for Electroencephalographic Information Detection.,» U.S. Patent, 1995b.
[2] F. LA e S. SS, «Using Brain MERMER Testing to Detect Concealed Knowledge Despite Efforts to Conceal,» J. of Forensic Sciences, vol. 1, n. 4, pp. 135-143, 2001.
[3] F. LA, «Method and Apparatus for Multifaceted Electroencephalographic Response Analysis (MERA),» U.S. Patent, 1994.
[4] K. Heckman e M. Happel, «Mechanical Detection Deception: A short Review,» in Educing Information: Interrogation: Science and Art, Washngton, DC: R. Swenson, 2006, pp. 63-94.
[5] M. D. Happel, J. A. Spitaletta, E. A. Pohlmeyer, G. M. Hwang, C. A. S. A. M. Greenberg e M. Wolmetz, «National Security and the Assessment of Individual Credibility: Current Challenges, Future Oppurtunities,» Jhons Hopkins APL Technical Digest, vol. 33, n. 4, 2017.
[6] R. Brandom, «Is ‘brain fingerprinting’ a breakthrough or a sham ? The controversial method claims to look inside a suspect’s brain to see the details of a crime- but hwo much can it see ?,» The Verge, 2015.
[7] S. A. Amir, «Brain fingerprinting: Dubai Police give exclusive glimpse at crime-fighting technology. A guilty suspect’s brainwaves can give them away if presented with an image, scene or weapon they have seen before,» The National, May 2021.
[8] I. Berlad e H. and Pratt, «“P300 in Response to the Subject’s Own Name”,» Electroencephalogr. Clin. Neurophysiol, vol. 96, n. 5, p. 472–474, 1995
[9] R. JP, B. JR, K. MJ e S. KM, «Subjective and objective probability effects on P300 amplitude revisited,» Psychophysiology, vol. 42, n. 3, pp. 356-359, 2005
[10] M. D. Comerchero e J. Polich, «P3a and P3b from typical auditory and visual stimuli” (PDF).,» Clinical Neurophysiology. , vol. 110, n. 1, p. 24–30., 1999.
[11] F. L.A., «Brain MERMERs: Detection of FBI Agents and crime-relevant information with the Farwell MERA system.,» in Proceedings of the International Security Systems Symposium, ,Washington, D.C., 1993.
[12] P. I. Series, Brain Fingerprinting: Ask the Experts, 2004.
[13] J. R. Evans, C. A. Meissner, S. E. Brandon, M. B. Russano e S. M. & Kleinman, «Criminal versus HUMINT interrogations: The importance of psychological science to improve interrogative practices,» Journal of Psychiatry & Law, n. 38, pp. 215-249, 2010.
Keywords
Prototype, design, First responder, uniform, First aid, a device for kids, Health condition, monitor for victims




